Encrypted Chat Application Design and Workflow
System Architecture
- Client
- Generates and manages RSA key pairs for encryption and decryption.
- Handles user authentication and session tokens.
- Encrypts messages using the recipient’s public key before sending them.
- Server
- Acts as a relay for encrypted messages.
- Stores and retrieves public/private keys and encrypted messages from the database.
- Facilitates secure key exchange between users.
- Database
- Stores encrypted private keys for retrieval, allowing multi-device access.
- Stores encrypted messages to ensure privacy.
- Uses encryption at rest and access control mechanisms.
Workflows
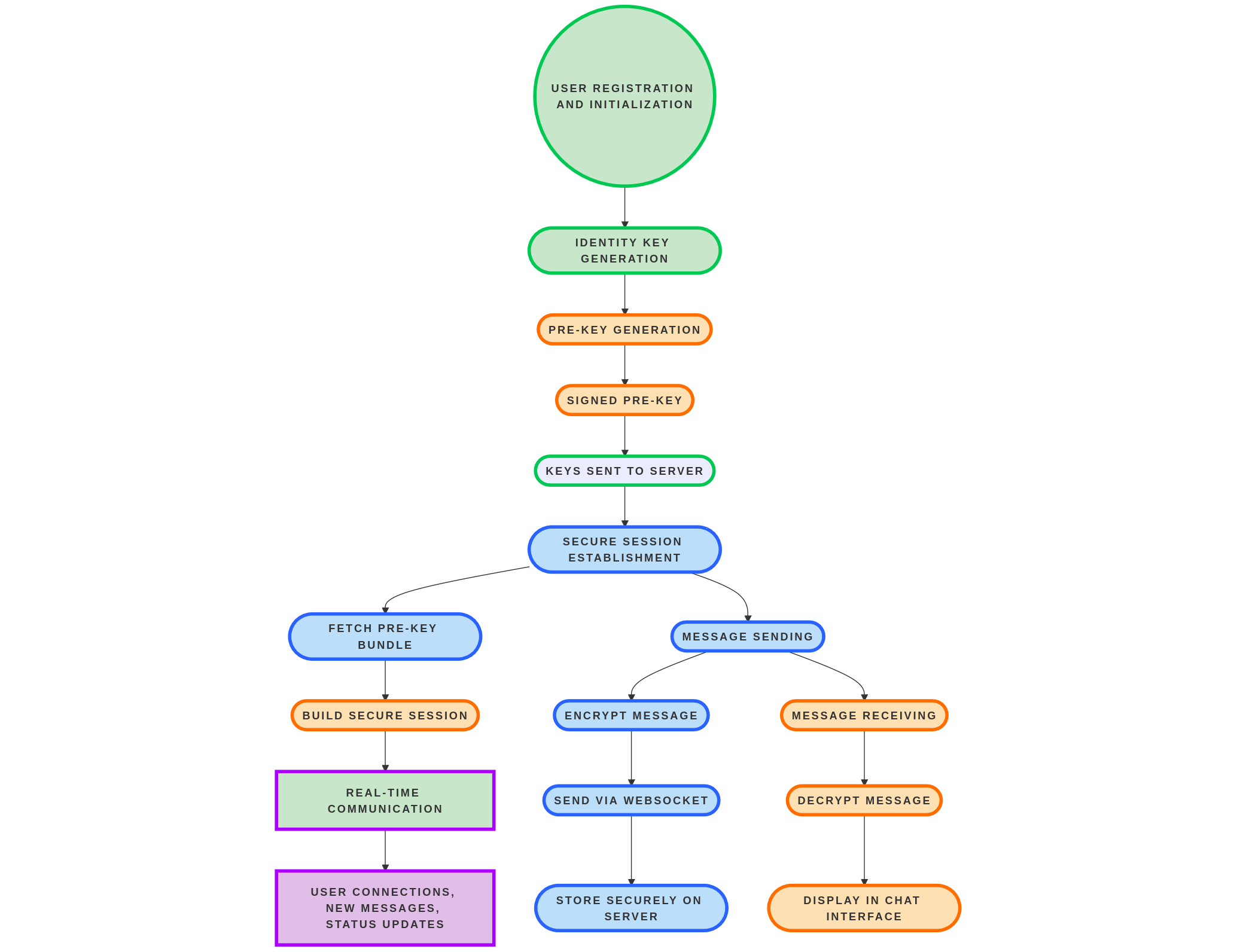
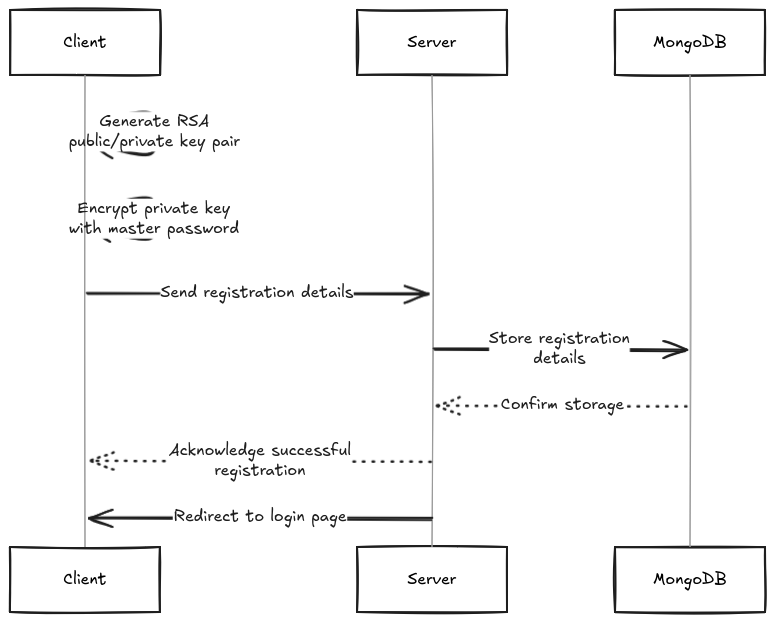
User Registration
- The user generates an RSA key pair locally.
- The public key is sent to the server.
- The private key is encrypted with the master password and uploaded to the server for recovery.
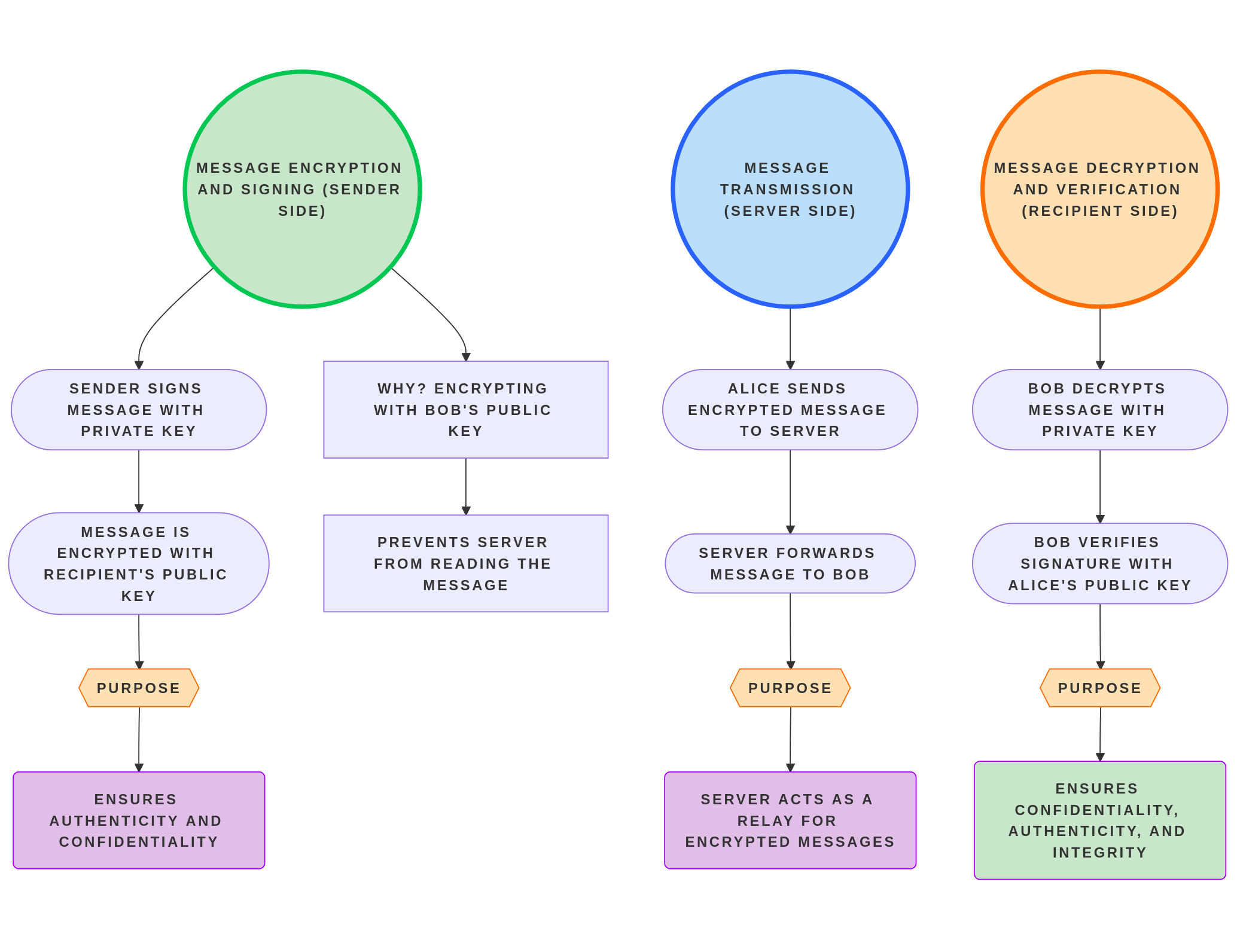
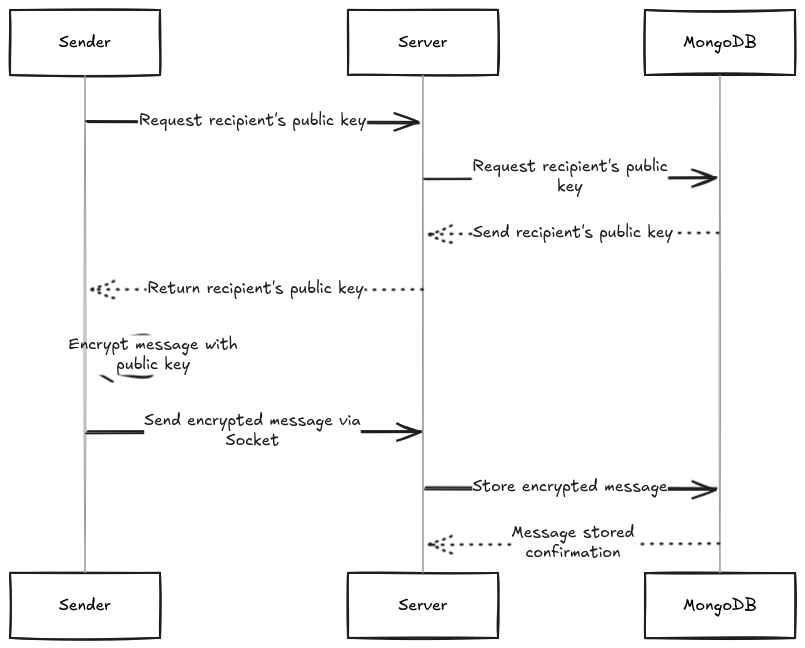
Sending a Message
- The sender requests the recipient’s public key from the server.
- The server retrieves the recipient's public key from MongoDB.
- The server returns the recipient's public key to the sender.
- The sender encrypts the message using the recipient’s public key.
- The encrypted message is sent to the server via a Socket connection.
- The server stores the encrypted message in MongoDB.
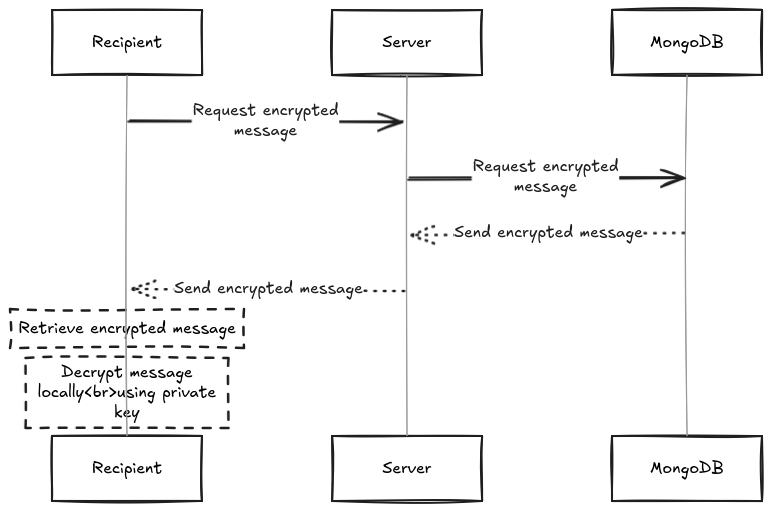
Receiving a Message
- The recipient requests the encrypted message from the server.
- The server fetches the encrypted message from MongoDB.
- The server sends the encrypted message to the recipient.
- The recipient decrypts the message locally using their private key.
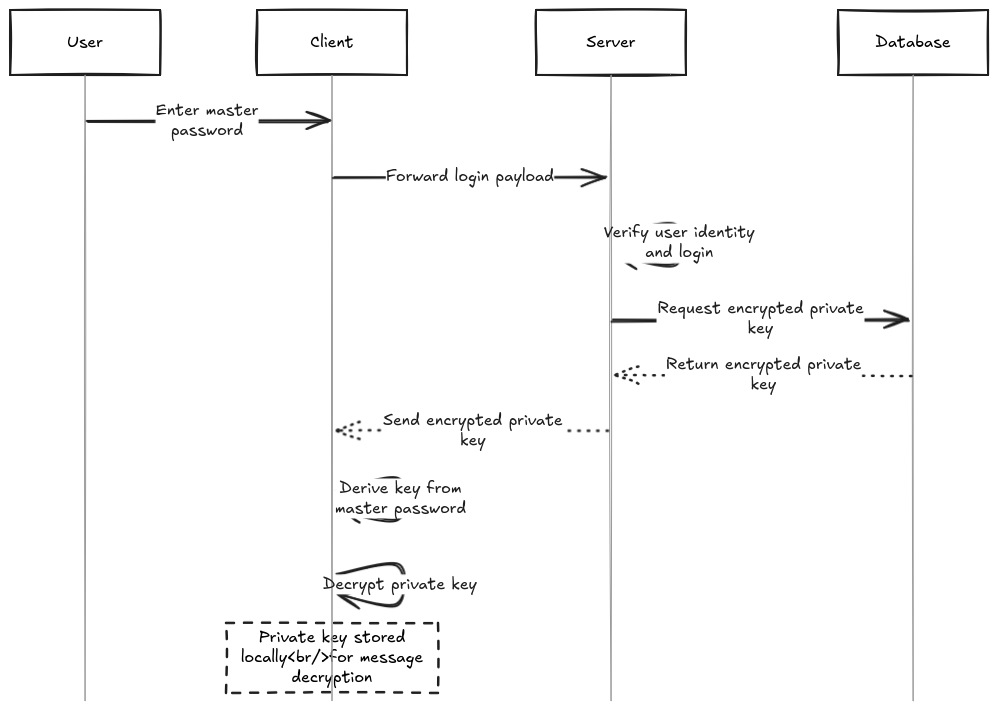
Multi-Device Support
- The user logs in with their master password.
- The client forwards the payload to the server for verification.
- The server verifies the user’s login.
- The server retrieves the encrypted private key from MongoDB.
- The user decrypts their private key locally using the derived key.
Vulnerabilities & Security Considerations
Potential Vulnerabilities
- Replay Attacks without session expiration.
- Password Recovery risk if the master password is compromised.
Potential Improvements
- Perfect Forward Secrecy (PFS) via the Signal Protocol to protect past messages even if keys are compromised.
- Zero-Knowledge Proof Authentication to ensure passwords are never revealed to the server.
Conclusion
This project provides a secure and privacy-focused messaging solution with end-to-end encryption. Future improvements will focus on enhancing security, usability, adding a TOR relay for IP anonymity, and robust password recovery.